Share: Decrypt .btc files
| GET BITCOIN CASH FROM BITCOIN CORE | 310 |
| PLACA DE BAZA PRO BTC | |
| Win 1 bitcoin free | How to get bitcoin cash using private key |
Avast releases free decryptor tool for BTCWare ransomware
Special thanks to Ladislav Zezula for working on this blog post and the decryptor tool!
If you’ve been hit by the BTCWare ransomware, you can now recover your files without paying the ransom. To decrypt your files, download Avast’s free decryptor tool here.
BTCWare ransomware began spreading in March 2017. Since then, we have seen five variants, that can be distinguished by the extension of encrypted files:
- foobar.docx.[sql772@aol.com].theva
- foobar.docx.[no.xop@protonmail.ch].cryptobyte
- foobar.bmp.[no.btc@protonmail.ch].cryptowin
- foobar.bmp.[no.btcw@protonmail.ch].btcware
- foobar.docx.onyon
Since its appearance, BTCWare has been using the FileName.Extension.[Email].Ext2 scheme of naming files. Recently, we saw a new variant, called Onyonware, that doesn’t include a contact e-mail address in the file name.
After execution, the ransomware generates a random password (one per machine), which is then used to create of the encryption key. The password is then encrypted with a public key (hardcoded in the binary) and presented as a User ID in the ransom files. The ransomware uses MS CryptoAPI to encrypting files - older samples use the RC4 cipher, newer ones (since May 2017) use AES-192.
The encrypted symmetric key is stored as a base64-encoded string %USERPROFILE%\Desktop\key.dat.
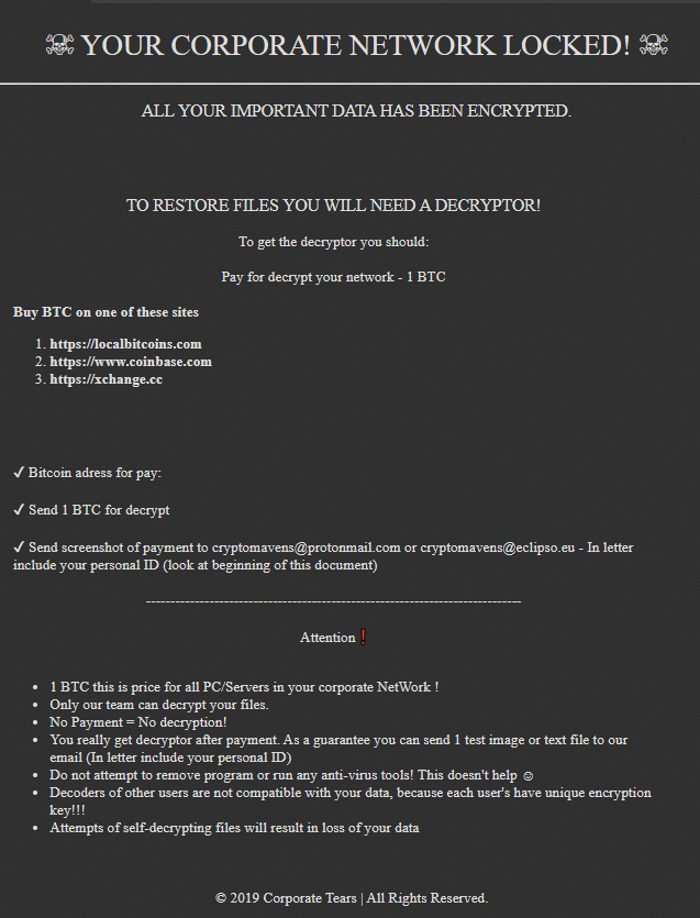
When the file encryption process is done, the ransomware changes the desktop wallpaper to the following picture:

Additionally, in each folder with at least one encrypted file, there is a #_README_#.inf or !#_DECRYPT_#!.inf file.


On May 16th, 2017, the master private key was published by BleepingComputer. The Avast BTCWare decryptor tool doesn’t use this key, because the key doesn’t work on all variants. Instead, a brute force is used to retrieve the password that has been used by the ransomware to encrypt files.
IOCs:
0c2830e7c6a5211ca77a7c312a823ad64e5c64903d652d532f4968ab164fb52d (.onyon)
1c74b5cc68758bfdc83b1b75d66201d811e27fb461448e11386b3eb9496600dc (AES-192)
1647973947121d42fd03814a5298975dfcc7cce4765f2cb4443cb8fe84ca9d88 (RC4)


-
-
-